As Telegram’s user base grows, so does its appeal to cybercriminals.

In the following, let’s discover the ingenious ways f#cking annoying hackers exploit public Telegram groups & supergroups to commit fraud, phishing, and distribute malware.
Now, let’s dive into the tactics these digital marauders employ…
Crypto Investment Scams
With the thriving popularity of decentralization, cryptocurrencies & blockchain in general, there are plenty of projects arise every single day.
P.S. At the moment of writing, Bitcoin reached its all-time-high of astonishing $71,734.30 🎯
But How Does it Work?
Well.
Hackers pose as experts or influencers within specific crypto communities, offering lucrative investment opportunities with guaranteed “1000% to the moon 🚀🚀🚀” returns.
Masquerading as the Elon Musks of the crypto world, casting themselves as saviors, they are ready to lead you to the promised land of exponential returns. But here’s the rub!
The promised land is nothing but a MIRAGE. Big beautiful empty MIRAGE.
Let’s briefly sum it all up.
Scammers attract people to the group XY ➡️ People lured into transferring their $$ ➡️ Scammers showcase fake profit margins ➡️ When enough $$ was collected, scammers DISAPPEAR with all the money!
Phishing Attacks via Custom Bots
Another very popular hacking tactic is deployment of sophisticated Telegram bots designed to mimic legitimate entities.
These bots engage users in conversation within groups, gradually earning their trust.
Eventually, the bot requests sensitive information (e.g. Credit Card number, Crypto Wallet phrase, etc.) under the guise of security verification or account updates.
An example of this method is the use of a bot named SMSRanger, which posed as representatives from well-known companies.
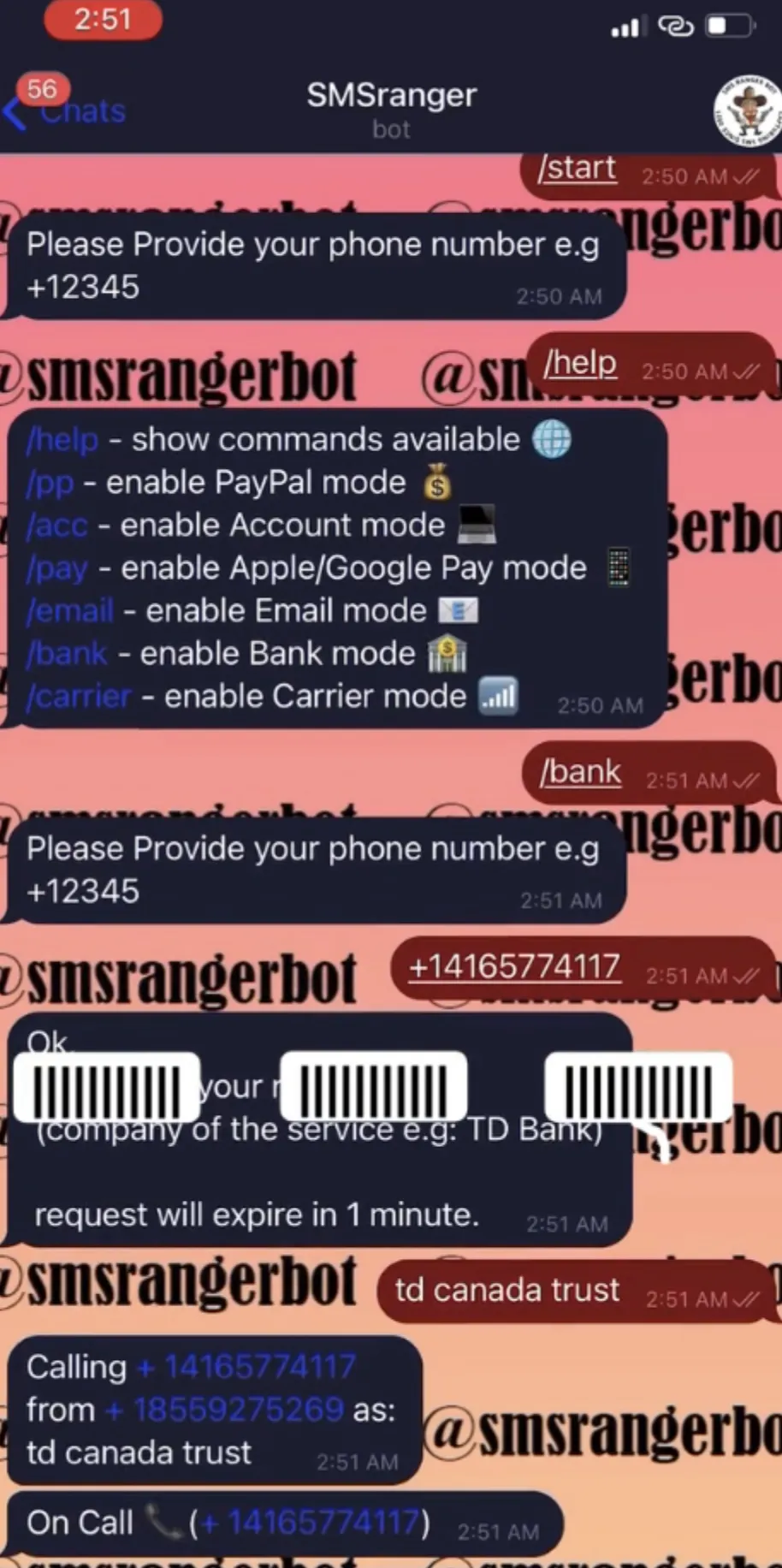
To briefly sum up how the SMSRanger works:
SMSRanger initiates contact ➡️ It claims to need verification details that included bank account logins, passwords, and 2FA codes, etc.
The realism of these bots, combined with the context of their deployment within trusted groups, significantly increases the risk of divulging sensitive information.
Last but not least, it’s extremely hard to spot the difference.
Scammers on forums claim that such bots are effective 80% of the time if a user answers the call. Even worse, anyone can get access to these bots and run scams for as little as $300 a month 🤯
If you’re looking to keep scammers & spammers out of your group, @GuardyShieldBot is the solution, offering unparalleled security and effortless management.
🛡️ Secure your community in 3 clicks with @GuardyShieldBot. Fast. Secure. Reliable 🛡️
Impersonation
It’s extremely common for hackers and scammers to impersonate Telegram users by choosing usernames that are very similar to, yet slightly different from, the originals.
Let’s consider an example: You’re an active participant in several crypto groups and are in active communication with one of the group moderators, who goes by the nickname @cryptomanager.
Suddenly, you receive a message from what appears to be a new account of his, stating that he decided to change his phone number and, therefore, opened a new account.
This is a scammer/spammer. It’s a classic impersonation scenario.
By creating a profile identical to the original, complete with the same profile picture and a username @cryptomanger, you could, without being aware of several red flags, lose your entire digital livelihood with a single misplaced chat, click, opened file, etc.
In 9 out of 10 cases.
Always ensure you know who you are communicating with. In the rush of the day, it’s easy to overlook such a mistake.
By the way, did you notice what was wrong? 😉
Remember, human error is the main cause of ❗95%❗ of all cybersecurity breaches. In other words, if human error were somehow eliminated entirely, 19 out of 20 cyber breaches might not have occurred at all (Source: IBM).

Make sure you report those accounts to official Telegram bot Report Impersonation, so that they get banned.
Takeaways
Below there’s a quick overview of some useful tips & red flags that’ll help you protect yourself from hackers, spammers and impersonators on Telegram.
- Be Aware of Common Scams on Telegram: Phishing links, impersonation scams, fake webpage scams, dating scams, fake giveaways, etc.
- Check Messages Carefully: Be skeptical of messages, especially from unknown contacts. Phishing and impersonation attempts may try to trick you into revealing personal information or sending money.
- Spot Fake Groups: Look for red flags like a large number of members, grammatical errors, requests for sensitive information, and use of fake logos. Enable Security Features: Use Telegram’s 2FA and passcode/Face ID verification to enhance your account’s security (even though it is not 100% secure)
- Use Secret Chats for End-to-End Encryption: Telegram’s secret chats offer end-to-end encryption, which is not enabled by default for all chats, unlike some other messaging apps.
- Be Cautious with Telegram Bots: While many bots are useful, some may be created by scammers. Verify the authenticity of a bot before interacting with it or providing any personal information.
- Disable Features That Risk Privacy: Turn off the “People Nearby” feature and never participate in the P2PL program unless necessary. Never share your geolocation or any other personal info.
- Block and Report Scammers: Don’t hesitate to block users who seem suspicious and report them to Telegram to help protect yourself and others. Use Report Impersonation for that (link above)
The general rule of thumb is to always think twice before:
- clicking on links
- sharing sensitive information (e.g. geolocation)
- opening any unknown files (even if they seems to come from a known contact or a legitimate organization).
That’s a wrap!
Thanks for reading! I hope you enjoyed it!